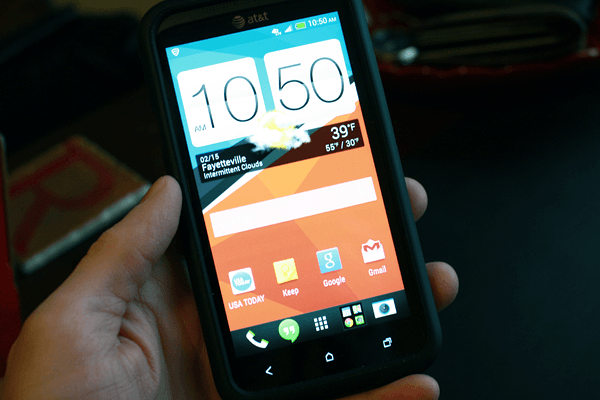
Last weekend I took the time to enable my phone’s WiFi and download Android 4.2.2 Jelly Bean. It has been a few months, but these days I rarely turn on WiFi on my device.
After a reboot, large download, and another reboot my phone initially looked like an HTC One. This experience was unfortunate but gave it a try for a couple days before switching to a more traditional look using an older HTC Clock/Weather widget.
My phone’s external case had broken, and couldn’t find a suitable deal on eBay so I went to the local mall bought an expensive replacement from a Cellairis booth. It isn’t a holster, but nonetheless very well-made.
- This is the last version HTC will support. At the time of this writing it is a year behind modern Android.
- This version of Jelly Bean is very clean, effective, and efficient.
- Setup and usage is effortless, it is essentially a new device. The OneX should have been this way from the beginning.
- With Chrome and LTE, it will rival many other larger devices in usability. Only higher-resolution tablets with LTE will provide a better experience.
I haven’t been pleased with the HTC One. Will likely try a Samsung or go out on my own with Nexus later this year.